Cybercriminals now tunnel their malicious data to your devices in a different way. It’s called “steganography”—and it involves hiding a document, video, or photograph inside another file that seems legit.
Until recently, hackers deployed cryptography to conceal online communication.
Now that encryption is relatively easy to detect, saboteurs increasingly hide their malevolence in plain sight—embedded in banner ads, text messages, or images. This is steganography, and it’s described as the digital equivalent of invisible ink.
Detecting the hidden data is like finding a needle in a haystack. The technique makes it easy for criminals to surreptitiously transmit data-stealing malware.
The threat is so serious that researchers formed a Criminal Use of Information Hiding (CUIng) Initiative, gathering experts from all over the world to learn ways to detect and disable information-hiding activity.
“A recent trend involves exploiting various information-hiding techniques to empower malware—for example, to bypass mobile device security frameworks or to exfiltrate sensitive data,” say the CUIng researchers and authors of “The New Threats of Information Hiding: The Road Ahead.”
One of the authors, Steffen Wendzel, discusses the discipline of steganography at the 9th annual Hack in the Box Security Conference held 9-13 April 2018 in Amsterdam.
In their report, the authors uncover real-world examples of existing and emerging threats using different data-hiding techniques.
Why steganography is on the rise
For a long time now, digital forensics experts have used sophisticated means of intercepting encrypted files and combing them for metadata—who is communicating with whom, when, and for how long—to catch criminals.
Such encryption receives a lot of attention from law enforcement and security professionals.
But criminals are getting smarter.
“Criminals or extremists are well aware of the increased focus on encryption and are looking for other ways to make malicious software stay under the radar, especially in the context of stealing data (where triggering some form of defense must be avoided). In this vein, the most important and recent trend is to equip malware with information-hiding capabilities, or techniques that hide communications,” say the authors.
How steganography works
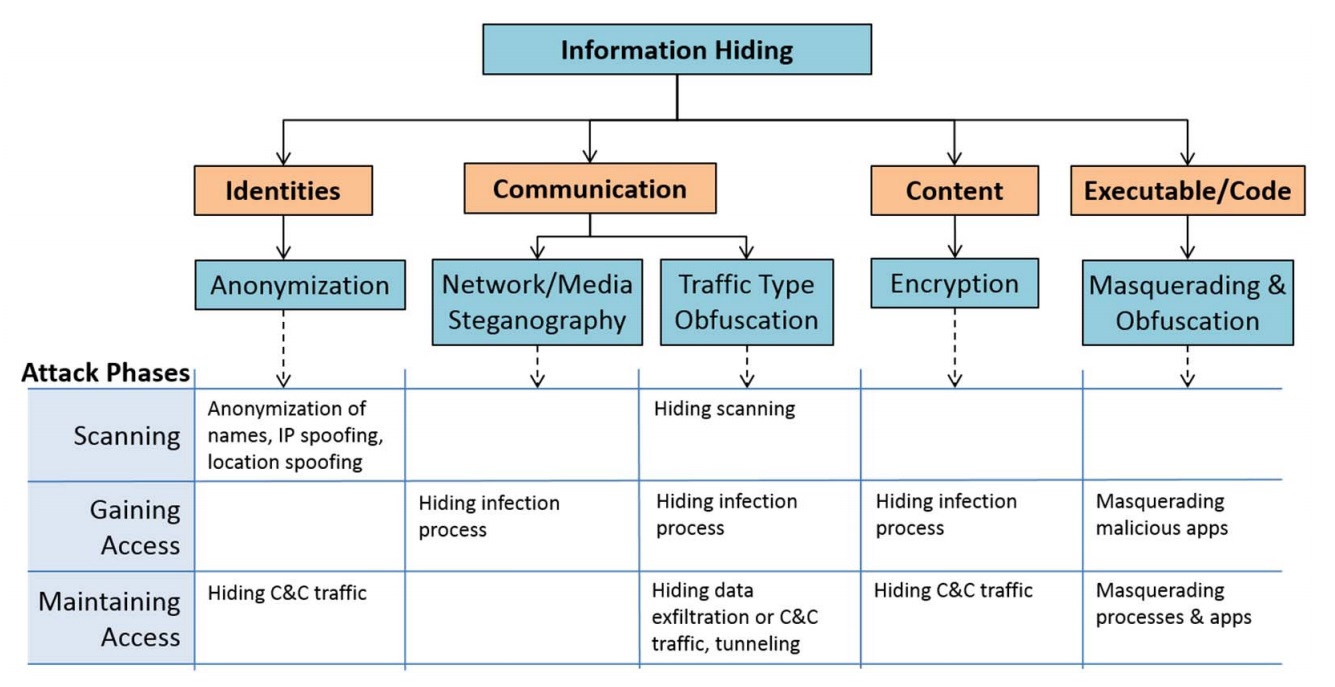
Criminals use steganography to hide information and communicate covertly with other criminals. Their goal is five-fold: scouting the target, scanning it, gaining access, staying undetected, and covering their tracks.
The chart below classifies information-hiding techniques and shows how they are used by malware in different attack phases.
Information hiding can also be used by an attacker during different attack stages depending on what information is being hidden:
- Identities. The identities of communicating parties are hidden by anonymization techniques.
- Communication. The fact that a communication is taking place is hidden by steganography techniques. The characteristics of a network conversation (for example, a packet flow) can be concealed using traffic-type obfuscation methods.
- Content. Hiding the content of data but not the transmission or presence of the data itself is achieved by applying cryptographic algorithms.
- Code. The structure of (executable) code is hidden by (binary) code obfuscation and masquerading techniques.
Real-world examples of information-hiding malware
In the table below, the authors present several examples of the most representative information-hiding malware observed “in the wild” from 2011 to 2017.
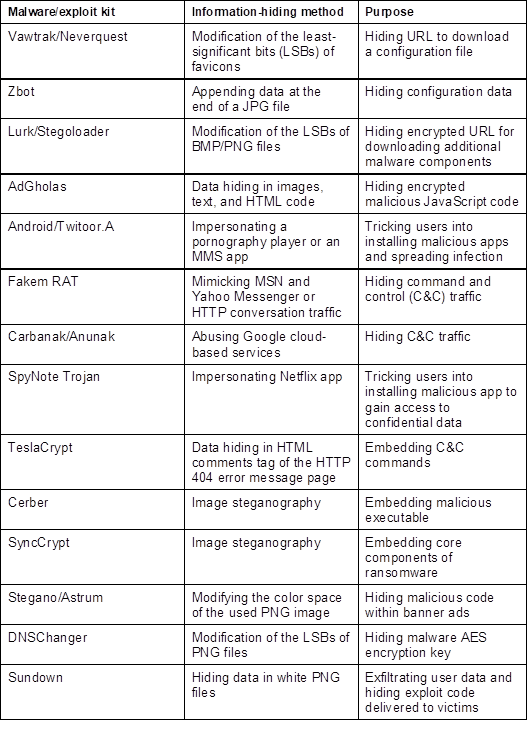 Originally, information-hiding techniques were used only in advanced persistent threats. However, according to the authors, information-hiding techniques are slowly becoming the de facto standard for “ordinary” malware.
Originally, information-hiding techniques were used only in advanced persistent threats. However, according to the authors, information-hiding techniques are slowly becoming the de facto standard for “ordinary” malware.
Where criminals hide information
The authors present several examples of where criminals can hide information:
Inside digital media files – At the end of 2016, large-scale attacks related to the online e-commerce platform Magento revealed the use of image steganography to conceal payment card details. Once the platform was infected, the malware collected payment details and hid them inside images of real products available on the infected e-commerce site.
Mimicking legitimate programs – One example is a variant of Android/Twitoor.A—malware that spreads by SMS or malicious URLs. The malware impersonates a pornography player or a multimedia messaging service application but without the correct functionality, eventually tricking the user to install the application and spread the infection.
Inside ransomware – In mid-2016, Cerber ransomware was identified as one of the macro-type malware-delivered ransomware across a variety of cloud-based file-sharing applications. To spread the infection, Cerber uses a decoy document which, when opened, loads a malicious macro-code that downloads a JPEG file to the targeted machine. The image holds a “steganographically-embedded malicious executable,” the authors say.
Inside an exploit kit – The first example of this is the Stegano/Astrum exploit kit, which was used in 2016 as part of a huge malvertising campaign. Malicious code is embedded within banner ads by modifying the color space of the PNG image (the alpha channel). Then, the victim’s browser parses an injected JavaScript code, extracting the malicious code, and redirecting users to the exploit kit landing page. The infection is performed on the landing page, typically by using several Flash vulnerabilities.
The road ahead
Cybercrime will continue to grow because it is very lucrative. Steganography threatens to exacerbate it.
“We see the following main developments in cybercrime: increased stealth, commoditization of malware, and exploitation of Internet of Things (IoT) devices. Cybercriminals will place more emphasis on making it harder to detect and trace back malware to its origin, which will be a main driver for the increased use of information hiding,” the authors say.
The authors believe that industry, academia, and law enforcement must work together to develop new tools to increase network security.
“Information hiding increases the complexity of addressing cybersecurity. Organized initiatives like CUIng can be the incubator where a long-term cure for information-hiding malware is developed, as modern cyberthreats require a multidisciplinary approach with the collaboration of many experts from industry, academia, and law-enforcement agencies,” they say.
The CUIng team of experts who wrote this article are and of the Warsaw University of Technology in Poland, of the National Research Council of Italy, of Worms University of Applied Sciences in Germany, of the University of Surrey in the UK, and of Murdoch University in Australia.
Research related to steganography in the Computer Society Digital Library:
- Exploring Steganography: Seeing the Unseen
- Hide and Seek: An Introduction to Steganography
- Digital Steganography: Hiding Data within Data
- A Novel Approach to Steganography in High- Dynamic-Range
- Detecting LSB Steganography in Color and Gray-Scale Images
- The Future of Digital Forensics: Challenges and the Road Ahead