As we step into a new era with billions of networked devices connected to cyberphysical systems, researchers say we will lose more control of our applications and private data.
That’s why computer scientists from the University of Helsinki and Tampere University of Technology are developing a novel programming model for a secure connectivity framework that protects data transmitted between the remote cloud and the network edge.
The research is centered on what they call the “Action-Oriented Programming” model, which is a trust system that reduces the chance of hacking into cloud, fog, and edge systems.
“The Action-Oriented Programming (AcOP) model and an associated framework can dynamically adapt to the edge and the cloud according to particular environment and connectivity conditions. Further, AcOP is compared to mobile-app-based and cloud-based CPS deployments,” write Niko Mäkitalo, Aleksandr Ometov, Joona Kannisto, Sergey Andreev, Yevgeni Koucheryavy, and Tommi Mikkonen, authors of “Safe, Secure Executions at the Network Edge: Coordinating Cloud, Edge, and Fog Computing” in IEEE Software magazine.
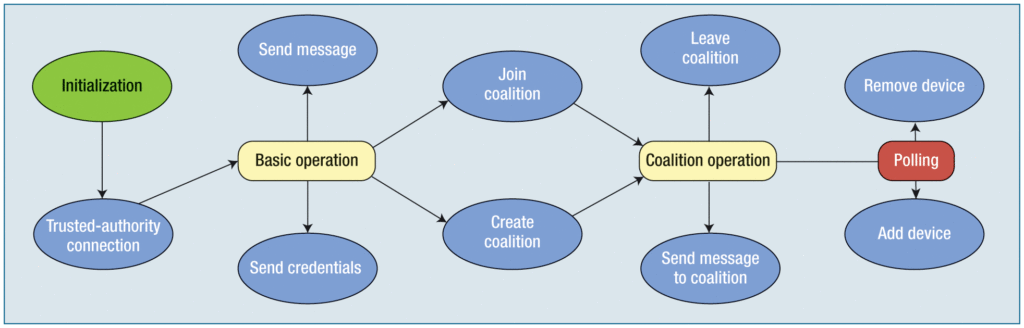
How Action-Oriented Programming (AcOP) works
When the Action-Oriented Programming (AcOP) model faces an emergency scenario, the user and device states (yellow and orange, in chart below) are reported to collective executions (light blue).
Actions (red) are coordinating the operation of various devices with capabilities (green). One device at a time acts as the coordinator, but the same software is executed collectively by multiple devices.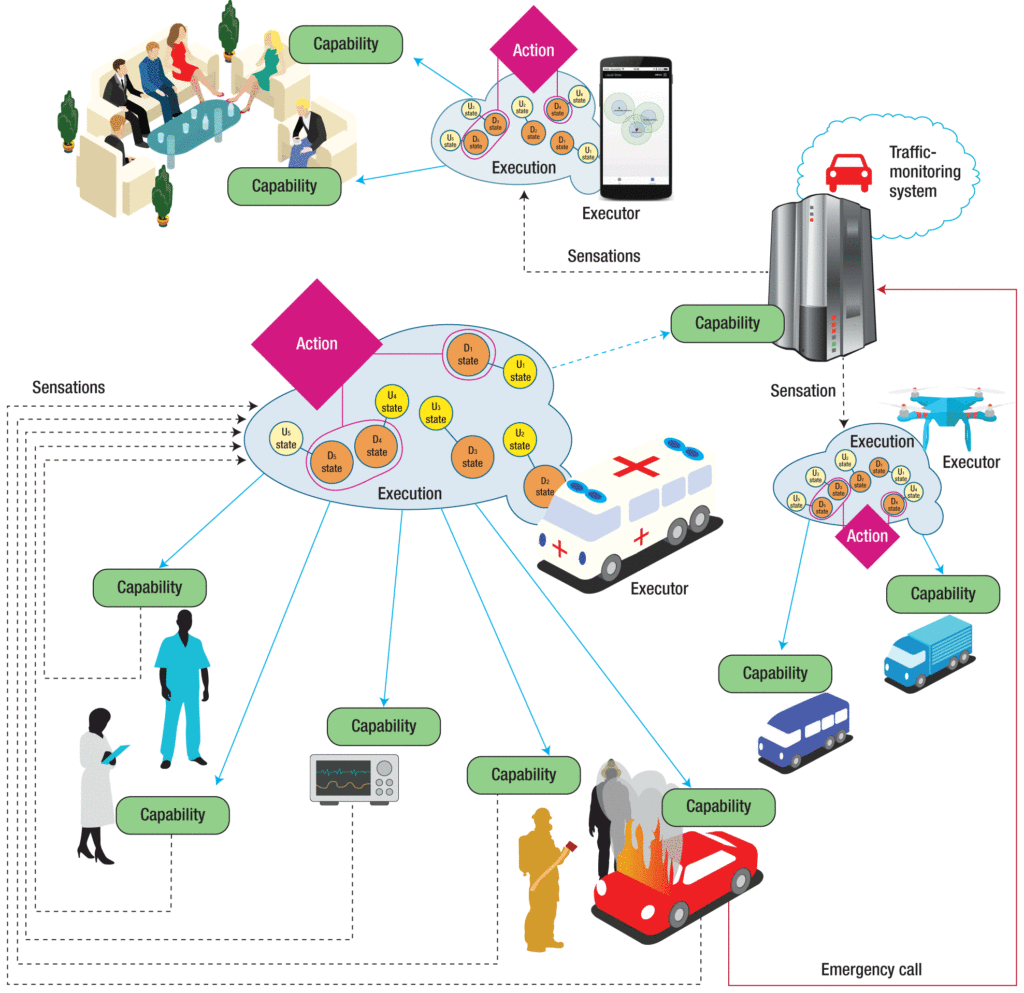
Structure of the coalitions operating behind AcOP’s collective executions
In the emergency scenario, execution in people’s devices enables them to seamlessly join and leave a coalition without disrupting collective execution.
“The only procedure that requires stable connectivity to the cloud is coalition initialization,” the authors say.
“First, the involved mobile devices receive their certificates with the corresponding secret and public keys. These are utilized to establish secure direct connectivity with each relevant device. When a device is willing to create a secure coalition with its ‘neighbors,’ a request containing the public identifiers of future coalition members is sent to the corresponding server. The coalition secret is then generated and split between the coalition users.”
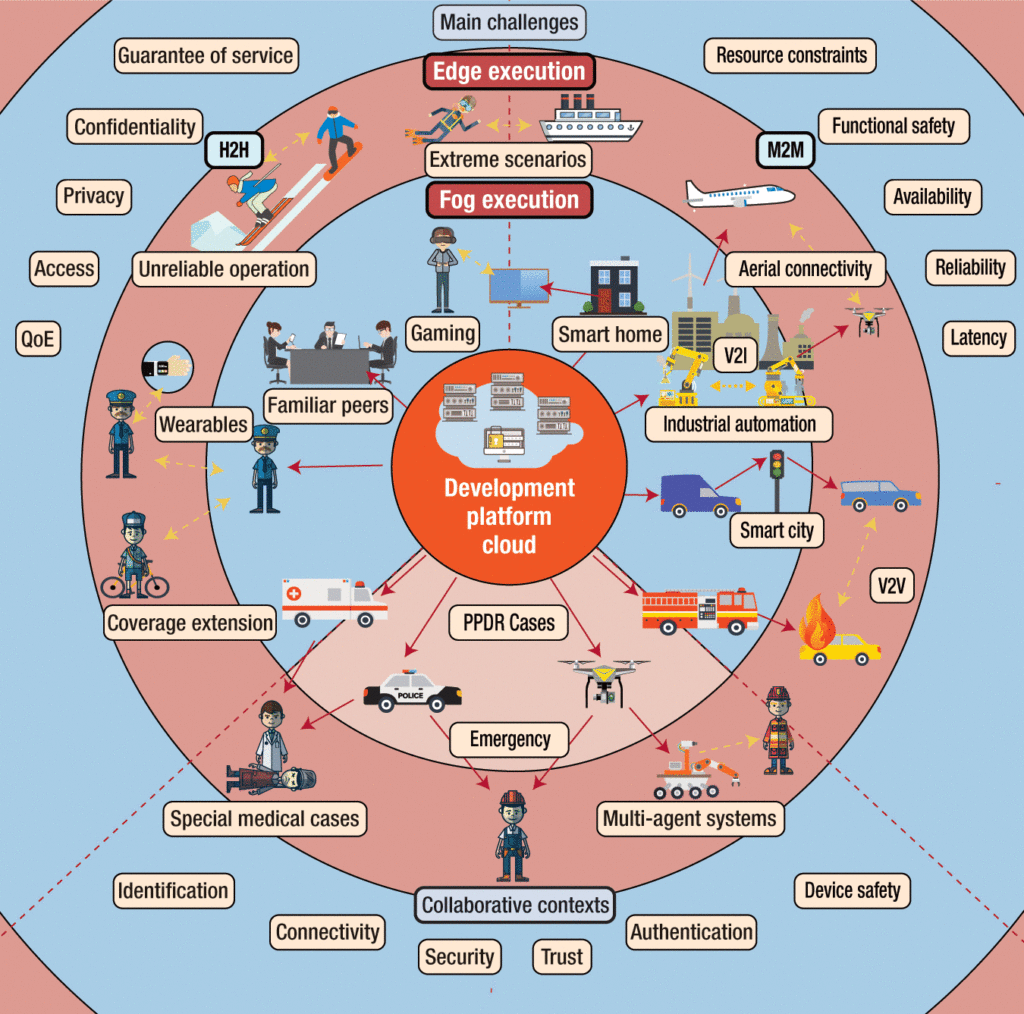
A grand illustration of cloud, fog, and edge computing for AcOP model
The authors illustrate the considered application scenarios of cloud, fog, and edge computing for the AcOP model at several levels:
- H2H = human-to-human
- M2M = machine-to-machine
- PPDR = public protection and disaster relief
- QoE = quality of experience
- V2I = vehicle-to-infrastructure
- V2V = vehicle-to-vehicle
A comprehensive chart analyzing Action-Oriented Programming model (A) for cyber-physical-system (CPS) development
The researchers provided an exhaustive analysis and commentary of how the Action-Oriented Programming model (A) for cyber-physical-system (CPS) development is compared with mobile-app (M) and cloud-service-based (C) approaches.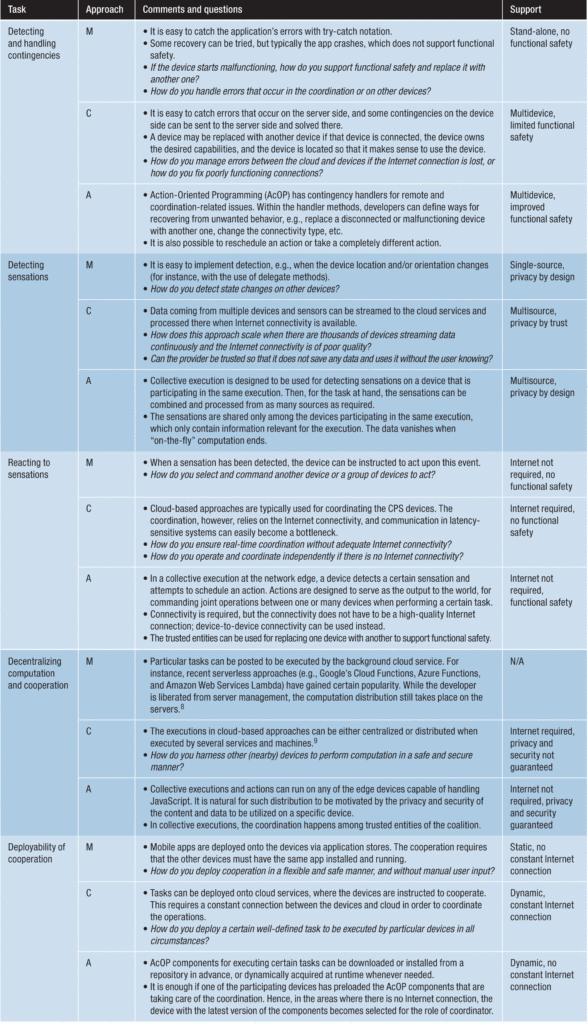
The more we relegate data processing and application functions to edge devices, the more we put our data at risk. The AcOP model intends to alleviate that.
“Edge computing is increasingly demanded due to the CPS requirements for increased scalability and functional safety—if the entities are coordinated by the cloud, the risk remains that without reliable Internet connectivity the functional safety cannot be guaranteed. In cooperation at the network edges, devices need to be able to trust each other, thus calling for dynamic coalitions with secure and trusted topology,” say the authors.
Related research on edge computing in the Computer Society Digital Library:
- Edge Computing
- The Promise of Edge Computing
- The Emergence of Edge Computing
- A Serverless Real-Time Data Analytics Platform for Edge Computing
- Edge Computing and the Role of Cellular Networks
- Real-Time Video Analytics: The Killer App for Edge Computing
- Virtual Edge-Based Smart Community Network Management
- Extending the Cloud to the Network Edge
- Edge Analytics in the Internet of Things